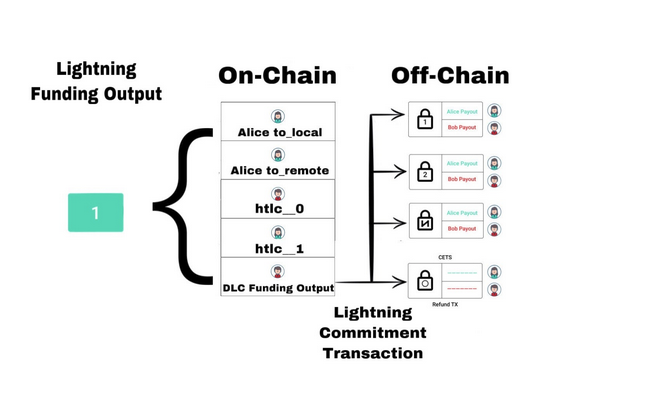
Recurring subscriptions on bitcoin implemented with DLCs
DLCs are typically thought to be used for betting. Alice & Bob want to speculate on an event, and have bitcoin payouts rewarded to them if they bet correctly. The oracle determines what event occurred and produces attestations representing …
Taproot funds burned on the bitcoin blockchain
We recently found a bug in how we parse taproot script pubkeys in our bitcoin-s library. When scanning the blockchain, an exception was thrown at block height 718448. The exception was thrown because this output does not properly conform to …
How to claim the 1BTC “Stable Channel” Bounty from HRF and Strike
Strike and HRF recently announced 3 bounties for development in the bitcoin ecosystem. The most interesting bounty in my opinion is the “stable channel” bounty. I tweeted out a thread on how to implement this on my personal twitter account, …
Krystal Bull Releases on Umbrel
We are releasing Krystal Bull on the Umbrel platform today. Krystal Bull is a Discreet Log Contract Oracle application. This is a crucial component to the DLC protocol. Oracles allow bitcoin bets to be settled based on real world events …
Hashrate derivatives with DLCs: Coinbase Put Contracts
Abstract This article explores how miners can hedge price volatility risk of bitcoin using Discreet Log Contracts for their freshly minted bitcoin in a coinbase transaction. The derivative explored in this article is having miners buying a put from a …
DLC Wallet Alpha Release
Today we are releasing the alpha version of our DLC wallet. This release contains all the primitives to execute arbitrary Discreet Log Contracts on the bitcoin blockchain. This wallet is self custodial which means you need to sync the chainstate …
DLCs vs Multisig: Censorship Resistance
One of the core value propositions of bitcoin is censorship resistance. As a result, bitcoin developers spend a lot of time thinking about how to design the protocol in such a way that is conducive to this goal. This blog …
DLC Oracle Failure Cases
Discreet Log Contracts (DLCs) are bitcoin-compatible non-custodial oracle contracts in which participants post Bitcoin collateral which is settled depending on an event in the “real-world” as attested to by a set of oracles. In this post, we will be exploring …
Multi-Oracle DLC Deep Dive
A couple weeks ago, we announced that we had successfully executed a DLC on-chain using oracles Bitfinex, Pierre Rochard and Suredbits. In this post, we will be diving into the details of how multi-oracle DLCs are accomplished. Before we dive into …
Settlement of First Multi-Oracle DLC
On March 11, 2021, Ben and I (Nadav) entered into a Discreet Log Contract on the bitcoin blockchain using a multi-oracle DLC. The oracles used were Bitfinex, Pierre Rochard and Suredbits. For the DLC to settle, 2 out of the …